SHA-2 vs. SHA-1: The Complete Rundown
Arc's Drummond® certification includes the optional SHA-2 profile, which was introduced to the testing in 2012. This addition ensures interoperability with partners using SHA-2 certificates and signatures. SHA-2 is more secure than SHA-1. This article answers common questions about the differences between SHA-1 and SHA-2. The article also explains the algorithms' roles in information security in regards to AS2.
What is SHA-2
SHA-2 is a family of hash algorithms that was created to replace SHA-1. SHA-2 actually consists of the SHA-224, SHA-256, SHA-384, and SHA-512 algorithms. SHA-256 is the most common implementation from this standard.
What is a hash algorithm? Why use SHA-2 in place of SHA-1?
SHA-2 and SHA-1 are one-way hashes used to represent data. The value of the hash will completely change if even a single byte of the data is changed, but the same set of data will produce the exact same result. This function only happens in one direction, however, as you can't look at a hash alone and tell what data was used to create the hash (The hash is usually short in comparison to the original data.).
The basic principle is that you can publicly compare two sets of data to see if they are the same without exposing that data for anyone to see. Each side calculates a hash over what they're comparing using the same known algorithm, and then the two results are compared. If a third party had tampered with even a single byte of the original data in between, the hashes would be completely different afterwards.
Because these hashes are one-way hashes, there's always the possibility that it is possible to assemble a random arrangement of bytes and produce a hash with the same result (known as a collision). This is highly improbable, difficult, and time consuming; however, it is still theoretically possible to produce a collision of a SHA-1 within the limits of existing technology. SHA-2 hashes are more secure; they use improved algorithms and larger hashes.
What is a SHA-2 certificate?
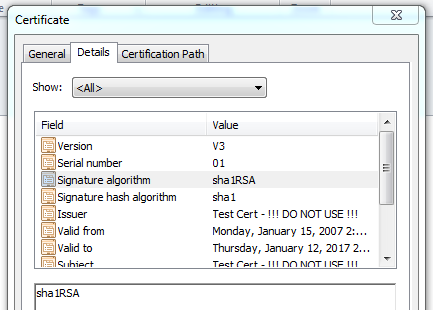
A certificate is a file store containing a key that's signed by the issuer of the key. If you inspect the Details tab of the certificate in Windows, you can see the signature algorithm that was used to sign the key.
A SHA-2 certificate is simply one where the signature algorithm used to sign the key is a SHA-2 algorithm (ex. SHA-256).
What is the difference between this and using the certificate to create a SHA-2 signature?
The certificate is a means of presenting a public key to your trading partners, but the keys themselves are going to be used to perform additional cryptography operations during the course of your communications. A private key can be used to sign a message for a partner, but the signature algorithm that is selected for that operation is not tied to the signing algorithm used to create the certificate. In this way, a SHA-1 certificate (like the certificate pictured above) can be used to sign a message using SHA-2, and- likewise- a SHA-2 certificate can be used to sign a message with SHA-1.
Okay, so what does my version of the application support?
Early versions of the AS2 Connector (Version 7 of the /n software IP*Works! EDI AS2 Connector and version 2 of the /n software AS2 Connector) do not support the creation or verification of SHA-2 signatures, but SHA-2 certificates can be configured in the application. Windows will validate the signature in the certificate, and the application will simply access the key therein.
Beginning with version 3 of the AS2 Connector and continuing on into Arc, the application supports both the configuration of SHA-2 certificates and the creation and verification of SHA-2 signatures. Please note, however, that SHA-2 signing is an optional protocol in AS2, and not all AS2 solutions support transmissions that were created with SHA-2 signatures.
Ready to get started?
Use Arc's free 30-day trial to start building your own custom workflows today:
